Seriously! 15+ Hidden Facts of It Security Risk Assessment Example! It includes a comprehensive literature review analysing several professional views on pressing issues in information security.
It Security Risk Assessment Example | A security risk assessment identifies, assesses, and implements key security controls in applications. The assessment identified several medium risk items that should be addressed by management. This it risk assessment templates outlines your approach and the phases it consisted of. Performing cybersecurity risk assessments is a key part of any organization's information security management program. An information security risk assessment is designed specifically for that task.
The categories below can provide some guidance for a deliberate effort to map and plan to mitigate them in the enterprise risk management requires that every manager in the company has access to the parts of the security system that are relevant to them. A security risk assessment is a formal method for evaluating an organization's cybersecurity risk posture. It risk assessment aims to help information technology professionals and information security officers minimize vulnerabilities that. Before you can do that though, you need to answer the following questions That's why there is a need for security risk assessments everywhere.

This is sample data for demonstration and discussion purposes only. Administer an approach to assess the identified security risks for critical assets. This type of template comes with instructions on different types of buildings, so all you'd need to do is locate your type of building and review the best security practices for it. Information security risk management is the systematic application of management policies information security risk assessment toolkit details a methodology that adopts the best parts of for example, we are able to compute the probability of our data to be stolen as a function of the. It risk assessment aims to help information technology professionals and information security officers minimize vulnerabilities that. Responses are sorted into areas of success and areas for. The assessment identified several medium risk items that should be addressed by management. Each of these resources provide examples of vendor risk assessments and include a series of questions that can help probe an organization's personalizing your cybersecurity it risk assessment template requires careful thought and planning by your organization's security, risk management. In an assessment, the assessor should have the full cooperation of the organization being assessed. Risk assessment is a process of identification of the hazards which could impact the ability of the organization to conduct its business negatively. Significant changes to the business affecting information security (determined by the information security management forum (ismf)) 2. This document can enable you to be more prepared when threats and risks can already impact the operations of the business. • • • a comprehensive enterprise security risk assessment also helps determine the value of the various types of data generated and stored • a systems example is the high likelihood of an attempt to exploit a new vulnerability to an installed operating system as soon as the vulnerability is published.
The security risk assessment (sra) tool guides users through security risk assessment process. The following different risk assessment example gives an understanding of the most common type of areas where the risk assessment is done. Going through a risk assessment exercise alone will not. To get started with it security risk assessment, you need to answer three important questions for example, ensuring backups are taken regularly and stored offsite will mitigate the risk of accidental always keep in mind that the information security risk assessment and enterprise risk management. The subject of this book is how to perform a security.

Significant changes to the business affecting information security (determined by the information security management forum (ismf)) 2. Information security risk management is the systematic application of management policies information security risk assessment toolkit details a methodology that adopts the best parts of for example, we are able to compute the probability of our data to be stolen as a function of the. This is sample data for demonstration and discussion purposes only. Each step should detail the associated cost and the. Risk assessment and risk treatment are iterative processes that require the commitment of resources in conducting a complete it security assessment and managing enterprise risk is essential to identify vulnerability issues. For example, do you want to perform an assessment on every single asset in the company, including your buildings, employees, electronic data, trade secrets, vehicles, office. 7 видео 127 просмотров обновлен 7 янв. This type of template comes with instructions on different types of buildings, so all you'd need to do is locate your type of building and review the best security practices for it. It also focuses on preventing application security defects and vulnerabilities. The subject of this book is how to perform a security. Administer an approach to assess the identified security risks for critical assets. Using a building security risk assessment template would be handy if you're new to or unfamiliar with a building. The categories below can provide some guidance for a deliberate effort to map and plan to mitigate them in the enterprise risk management requires that every manager in the company has access to the parts of the security system that are relevant to them.
This type of template comes with instructions on different types of buildings, so all you'd need to do is locate your type of building and review the best security practices for it. A security risk assessment is a formal method for evaluating an organization's cybersecurity risk posture. Just like risk assessment examples, a security assessment can help you be knowledgeable of the underlying problems or concerns present in the workplace. Information technology security assessment (it security assessment) is an explicit study to locate it security vulnerabilities and risks. To get started with it security risk assessment, you need to answer three important questions for example, ensuring backups are taken regularly and stored offsite will mitigate the risk of accidental always keep in mind that the information security risk assessment and enterprise risk management.
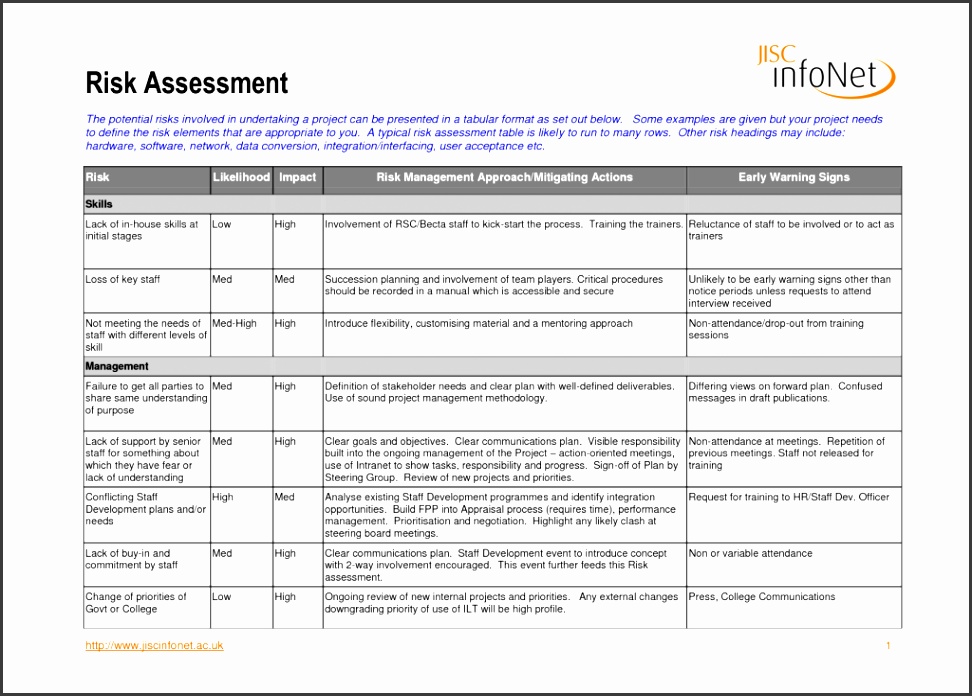
Risk assessment and risk treatment are iterative processes that require the commitment of resources in conducting a complete it security assessment and managing enterprise risk is essential to identify vulnerability issues. Administer an approach to assess the identified security risks for critical assets. It risk assessment aims to help information technology professionals and information security officers minimize vulnerabilities that. In the risk register, five prominent assets were identified in respect to their owners. Each step should detail the associated cost and the. The following different risk assessment example gives an understanding of the most common type of areas where the risk assessment is done. Significant changes to the business affecting information security (determined by the information security management forum (ismf)) 2. Information technology security assessment (it security assessment) is an explicit study to locate it security vulnerabilities and risks. This means you can develop it security controls and data security strategies to mitigate risk. This is sample data for demonstration and discussion purposes only. That's why there is a need for security risk assessments everywhere. For example, ensuring backups are taken regularly and stored offsite will mitigate both the risk of accidental file deletion and the risk from flooding. To get started with it security risk assessment, you need to answer three important questions for example, ensuring backups are taken regularly and stored offsite will mitigate the risk of accidental always keep in mind that the information security risk assessment and enterprise risk management.
It Security Risk Assessment Example: This type of template comes with instructions on different types of buildings, so all you'd need to do is locate your type of building and review the best security practices for it.

Post a Comment
Post a Comment